In June 2023 I Posted This Clip To Social Media. I Called Out The Many Types Of Personal Attacks On President Trump, Like: Hateful Rhetoric, Yellow Journalism, And Liberal Lawfare. Now We Can Add Attempted Assassination.
Category Archives: Terrorism Information

RNSK Vol 2, Edition 2
United States Supreme Court Decision: U.S. v Abu Zubaydah Published March 3, 2022
An Important Decision In Protecting Classified National Security Information
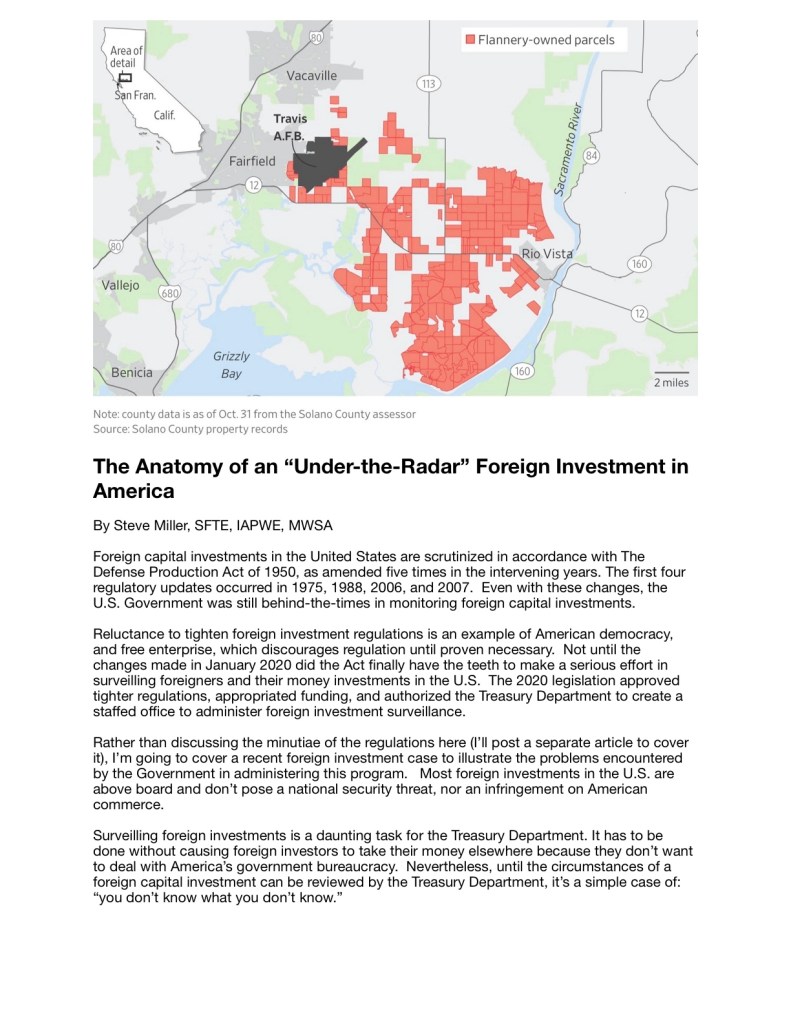
Introduction
The Zubaydah case has significant National Security implications, and the Court ruled in favor of the United States. For most people, court cases can be pretty boring, and even more so at the Supreme Court level; unless, of course, you are fascinated by legal proceedings like me.
In the Zubaydah case, a common court procedure, “discovery,” became a critical issue that could have had a major effect on national security. In criminal cases, it sometimes becomes important for the prosecution or defense to prove or disprove the physical presence of a person involved in the case in order to establish a defendant’s guilt or innocence. However, a person’s physical presence at a certain location, or their whereabouts, is not always material to the case; this includes the location of someone when evidentiary information was obtained from them. For example, if a murderer confesses to a murder while in the back of the patrol car heading to jail, the fact that it occurred in the car makes no difference to its admissibility than if the defendant confessed to it in a police station interrogation room. In Zubaydah’s case, one of the attorneys-of-record decided to file a motion for discovery to determine Zubaydah’s physical presence at a certain location where his testimony/confession had been disclosed. This discovery motion is what stirred up national security concerns.
Background of the Case
Zubaydah is currently a detainee at the Guantanamo Bay Detention Facility. Zubaydah was a senior Al Qaeda lieutenant who was sought in connection with the World Trade Center Attack in September 2001. He was ultimately caught in 2002 and remanded to U.S. custody. During Zubaydah‘s detention in 2010, he filed a lawsuit against the USG, alleging that in 2002-2003 he was held by the CIA at a “black site” in Poland. His lawsuit complained that he was unlawfully detained at the black site, citing the Supreme Court decision that enhanced interrogation techniques were illegal, as well as, unlawful detention, which prejudiced his criminal arrest warrant for conspiracy in the 9-11 attacks, and therefore any information which may have been obtained from Zubaydah was inadmissible; ergo his case ought to be dismissed.
Zubaydah had/has multiple criminal charges pending, with some relying on the confession/testimony he alleged came from his black site detention. Although Zubaydah’s black site claim might get the charges dropped that relied on information obtained at the black site, it would not affect other pending charges that did not rely on that information. Sometimes a key factor in a criminal case is proving/disproving the defendant was/was not physically present at the location(s) where events of the case may have occurred. In the case of Zubaydah, the information he revealed at the alleged Polish black site had been confirmed by the USG as valid, but that was not as important as the alleged location where information was obtained.
U.S. District Court Activities
When the district court considered the defense’s discovery motion, which requested the CIA disclose the location where the defendant’s confession/testimony was obtained, the prosecutors declined to confirm/deny anything about a Polish black site, citing that CIA methods & trade craft are classified information that may harm U.S. national security if revealed. Prosecutors stated that it was common practice by the USG that when the public requested information, or asked for corroboration of certain information already in the public domain, which may or may not have classified national security implications, the USG may choose to reply that they cannot confirm or deny what was being asked for. Prosecutors further stated that there was no statute or case law that compelled the USG to declassify and disclose classified national security information based on a formal or informal request, regardless if the requestor alleges the information is already public knowledge. The prosecution moved to dismiss the discovery motion. The District Court judge concurred with the CIA, dismissing Zubaydah’s discovery motion, as well as dismissing the defense’s lawsuit against the CIA. None of these proceedings had any immediate affect one way or the other on pending criminal charges against Zubaydah, and other defendants, that stemmed from the alleged Zubaydah black site interrogation.
U.S. Court of Appeals Activities
Zubaydah’s attorneys appealed the lower court decision to dismiss the discovery motion, and the lawsuit, to the 9th Circuit Court of Appeals. Zubaydah’s attorney’s submitted that once classified information is found in the public domain, which was alleged to be the case about the black site’s existence, it was no longer sensitive, national security-classified information. In layman’s terms, it was like “the-cat-was-already-out-of-the-bag,” so what’s the big deal? The Appeals Court agreed with the defendant, and reversed the District Court’s ruling, agreeing that once the information was in the public domain, it was moot to retain a national security classification. Reversing the lower court’s dismissal of the discovery motion, and lawsuit, meant the USG could be compelled to acknowledge the black site’s existence in Court, and any details about it. The case was remanded back to the District Court, where Zubaydah’s attorneys would compel the CIA to reveal the black site’s existence, and therefore move to dismiss criminal case(s) based on the Supreme Court’s prior ruling that black site detention locations and enhanced interrogation techniques were unconstitutional.
U.S. Supreme Court Activities
Before the District Court judge could rule on reversing the dismissal of the discovery motion, and lawsuit, based on Appeals Court guidance, CIA lawyers sought an injunction from the Supreme Court until they could rule on the merits of the motion-to-dismiss. The injunction was granted, allowing time for the case to be heard by The Supreme Court. After the prosecution and defense argued their cases in front of the Court, the Court issued a ruling in favor of the CIA. The Court opinion noted that it has been standard USG practice that if any sort of classified information has been disclosed to the public, the USG is not required to confirm or deny anything about the alleged classified information, since it was classified by the USG in the first place.
Basically, just because alleged classified information has been leaked to the public, the U.S. Government is not required to comment or corroborate the leaked information. This would be a kin to releasing photos to the public of a man standing on the sidewalk near a bank that was being robbed, with the photo clearly showing he was looking right at the robbers as they exited the bank to leave in their getaway car. Speculation was rampant on social media that the man in the photo was a well-known baseball player, but the picture was grainy, and no one was 100% positive it was him. If a discovery motion was filed by the prosecution to compel the baseball player to admit it was him in the picture, and thereby subpoena him to testify against the robbers, but the player is not being charged or investigated for wrongdoing, there’s no statute or case law that says he is required to confirm his identity.
The concept here that applies to national security information is that if it is leaked to the public, the USG cannot be compelled to publicly acknowledge the veracity of the information, nor whether it carries a national security classification, if any. Had the Supreme Court allowed that any alleged USG privileged information that was compromised to the public, could compel the USG to confirm or deny it, if so requested, could cause unintended harm to others. This would mean that such information as might appear on Wikileaks, for example, anyone could submit a formal request to USG compelling them to disclose the veracity of the information.
Aftermath of the Supreme Court Ruling
In the Zubaydah case, the defense attorneys were quite shrewd. By filing a discovery motion seeking to compel the USG to confirm or deny the site, whatever the outcome, the cases stemming from the information obtained at the black site would end up being dismissed. If the CIA confirmed the black site’s existence and the information obtained there, those cases would be dismissed, BUT more importantly, it would have damaged the Polish government in the court of public opinion for allowing the black site operation, as well as, destroy any trust between the two governments. Alternatively, if the CIA denied the black site’s existence, they would be committing perjury, which has no statute of limitations. Poland’s reputation would remain intact, and Zubaydah would likely have been convicted of the crimes stemming from the black site-obtained information. The third option, which was allowed by the Supreme Court, gave the CIA the ability to use the standard reply in these situations – that the information could not be confirmed or denied. This kept Poland’s reputation intact, and did not require the USG to corroborate classified information in the public domain. Unfortunately, the third option meant the District Court’s dismissal of the defense’s discovery motion might create doubt as to the validity of the information if it were utilized in a jury trial. The defense would show the jury that the prosecution could not testify as to where or how the incriminating information was obtained, thereby casting suspicion on the veracity of it. The jury would learn the USG was hiding something, and be unlikely to convict someone using evidence that may have been obtained illegally. So, rather than chase down that rabbit hole, the prosecution had no choice but to concur with the judge’s ruling to dismiss the case(s) using the black site information. Zubaydah still had many other charges pending based on other evidence, but the defense attorney’s very shrewdly got rid of a sizable chunk of the court cases against Zubaydah. Other defendants implicated in Zubaydah’s black site testimony also had some charges dropped.
The moral to this story is that a democratic form of government has a lot more plusses than minuses. In order to have the benefit of all of the favorable aspects of living in the United States, there are going to be times that you have no choice but to accept the bad. No one really doubted Zubaydah’s guilt; he would be convicted on other charges stemming from different information sources. But to get a conviction (a good outcome of democracy) on Zubaydah’s black site confession, it would have required representatives of the U.S. Government to lie under oath (a bad choice), which is not how a democracy works. Zubaydah and his attorneys relied on the fact America’s democratic-based legal system would get him off-the-hook.
Ciao,
Steve Miller, IAPWE – Certified & Member
Managing Editor
The Report on National Security Kinetics™
Seattle, WA. USA
vietvetsteve@millermgmtsys.com
RNSK Vol I, Edition 5
September 3, 2020
Transnational Organized Crime: What Makes It An American National Security Interest?
 photo courtesy of Global Financial Integrity
photo courtesy of Global Financial Integrity
Introduction
The expanding size, scope, and influence of transnational organized crime and its impact on U.S. and international security and governance represents one of the most important challenges to nearly every country. During the past 20 years, technological innovation and globalization have proven to be an overwhelming force for good. However, transnational criminal organizations have taken advantage of our increasingly interconnected world to expand their illicit enterprises.
Threat Risks From Transnational Organized Crime
• Penetration of Foreign Government Institutions, Corruption, and Threats to Their Governance. Developing countries with weak rule of law can be particularly susceptible to Transnational Organized Crime (TOC) penetration. TOC penetration of states is deepening, leading to co-option in a few cases and further weakening of governance in many others. The apparent growing nexus in some states among TOC groups and elements of government—including intelligence services—and high-level business figures represents a significant threat to economic growth and democratic institutions.
• Threats to the Economy, U.S. Competitiveness, and Strategic Markets. Transnational Organized Crime threatens U.S. economic interests and can cause significant damage to the world financial system through its subversion, exploitation, and distortion of legitimate markets and economic activity. U.S. business leaders worry that U.S. firms are being put at a competitive disadvantage by Transnational Organized Crime and corruption, particularly in emerging markets where many perceive that rule of law is less reliable. The World Bank estimates over $1 trillion is spent each year to bribe public officials, causing an array of economic distortions and damage to legitimate economic activity. The price of doing business in countries affected by Transnational Organized Crime is also rising as companies budget for additional security costs, adversely impacting foreign direct investment in many parts of the world.
• Crime-Terror-Insurgency Nexus. Terrorists and insurgents increasingly are turning to Transnational Organized Crime to generate funding and acquire logistical support to carry out their violent acts. The Department of Justice maintains a classified report known as the Consolidated Priority Organization Targets (CPOT) list. The last time CPOT was declassified via a FOIA request was 2015. That edition of the CPOT listed a total of 63 organizations, 29 of which, are significant international drug trafficking organizations (DTOs) that threaten the United States, AND have links to terrorist groups. Involvement in the drug trade by the Taliban and the Revolutionary Armed Forces of Colombia (FARC) has been critical to the ability of these groups to fund terrorist activity. The U.S. Law Enforcement and Intelligence Community is concerned about Hezbollah’s drug and criminal activities, as well as indications of links between al-Qaeda in the Lands of the Islamic Maghreb and the drug trade. Further, the terrorist organization al-Shabaab has engaged in criminal activities such as kidnapping for ransom and extortion, and may derive limited fees from extortion or protection of pirates to generate funding for its operations. ISIS has also been very active in the TOC arena.
• Expansion of Drug Trafficking. Despite demonstrable counter-drug successes in the past 8-9 years, particularly against the cocaine trade, illicit drugs remain a serious threat to the health, safety, security, and financial well-being of Americans. The demand for illicit drugs, both in the United States and abroad, fuels the power, impunity, and violence of criminal organizations around the globe. Mexican DTOs have escalated their violence to consolidate their market share in the Western Hemisphere, protect their operations in Mexico, and expand their reach into the United States. In West Africa, Latin American cartels are exploiting local criminal organizations to move cocaine to Western Europe and the Middle East. Kenya, in Eastern Africa, has become a major distribution hub for heroin coming from Afghan DTOs to Europe and the United States. Many of the well-established organized criminal groups that had not been involved in drug trafficking—including those in Russia, China, Italy, and the Balkans—have now established ties to drug producers to develop their own distribution networks and markets.
• Human Smuggling/Trafficking. Human smuggling is the facilitation, transportation, attempted transportation, or illegal entry of a person or persons across an international border, in violation of one or more country’s laws, either clandestinely or through deception, whether with the use of fraudulent documents or through the evasion of legitimate border controls. It is a criminal commercial transaction between willing parties who go their separate ways once they have procured illegal entry into a country. The vast majority of people who are assisted in illegally entering the United States and other countries are smuggled, rather than trafficked. International human smuggling networks are linked to other transnational crimes including drug trafficking and the corruption of government officials. In the past few years trafficking in children has begun to pick-up.
• Weapons Trafficking. Criminal networks and illicit arms dealers also play important roles in the black markets from which terrorists and drug traffickers procure some of their weapons. As detailed in the 2010 UN Organization on Drugs & Crime report, The Globalization of Crime (Note: this report was a massive undertaking and cannot be replicated yearly, however a new one was in preparation for 2020 before the COVID-19 Pandemic, so it is unlikely to be published this year), the value of the documented global authorized trade in small arms (i.e.; handguns, rifles, shotguns, machine guns) has been estimated at approximately $2.08 billion in 2010, with unrecorded but legal transactions making up another $120 million or so. The most commonly cited estimate for the size of the illicit market is approximately 20% of the legal market. According to the head of UNODC, these “illicit arms fuel the violence that undermines security, development and justice” worldwide. U.S. Federal law enforcement agencies have intercepted large numbers of weapons or related items being smuggled to China, Russia, Mexico, the Philippines, Somalia, Myanmar, Mali, Somalia, Turkmenistan, Syria and Yemen. It is important to note this discussion does NOT include heavier weaponry, such as: Rocket Propelled Grenades, anti-tank rockets, heavy barrel machine guns (like the U.S. M2 .50 caliber machine gun, for example), fragmentation grenades, 40mm grenade launchers, mortars & field artillery.
• Intellectual Property Theft. TOC networks are engaged in the theft of critical U.S. intellectual property, including through intrusions into corporate and proprietary computer networks. Theft of intellectual property ranges from movies, music, and video games to imitations of popular and trusted brand names, to proprietary designs of high-tech devices and manufacturing processes. This intellectual property theft causes significant business losses, erodes U.S. competitiveness in the world marketplace, and in many cases threatens public health and safety. Between FY 2003 and FY 2010, the yearly domestic value of customs seizures at U.S. port and mail facilities related to intellectual property right (IPR) violations leaped from $94 million to $188 million. Products originating in China accounted for 66% of these IPR seizures in FY 2010. Estimates for 2020 are in excess of $450 million, and China still leads the pack.
• Cybercrime. TOC networks are now significantly involved in cybercrime, as it has become increasingly difficult to launder money, and/or defeat institutional security systems which are controlled by networked computer systems. Cybercrime costs consumers tens of billions of dollars annually, threatens sensitive corporate and government computer networks, and undermines worldwide confidence in the international financial system. Through cybercrime, transnational criminal organizations pose a significant threat to financial and trust systems—banking, stock markets, e-currency, and value and credit card services—on which the world economy depends. For example, some estimates indicate that online frauds perpetrated by Central European cybercrime networks have defrauded U.S. citizens or entities of more than $1 billion in a single year. According to the U.S. Secret Service, which investigates cybercrimes through its 31 Electronic Crimes Task Forces, financial crimes facilitated by anonymous online criminal elements, result in billions of dollars in losses to the Nation’s financial infrastructure. The National Cyber Investigative Joint Task Force, led by the Federal Bureau of Investigation (FBI), functions as a domestic focal point for 18 federal departments or agencies to coordinate, integrate, and share information related to cyber threat investigations, as well as make the Internet safer by pursuing terrorists, spies, and criminals who seek to exploit U.S. system.
• Information Warfare. The 2016 Presidential Election demonstrated that shadowy foreign government agencies, in concert with private TOC groups, have a significant capability of committing Information Warfare by exploiting America’s open society and means of mass communication. Common social media platforms, such as YouTube, Twitter, Instagram, TikTok, SnapChat, Facebook, Google, and others, have been infiltrated to influence public thinking. Other aspects of criminal information warfare include developing misleading documents, such as the now debunked dossier procured by the Democratic National Committee that attempted to implicate the Trump Campaign in colluding with Russia to rig the election. This dossier was actually used as evidence by the FBI to get a warrant to tap the phones of a Trump Campaign staffer. We are seeing just the tip of the iceberg in TOC involvement in information warfare. The allure of adversary governments using TOCs for these activities is simple: TOCs are adept at working in the shadows, below the radar, because getting caught is not as big of a problem as losing tens or even hundreds of millions of dollars in the process. TOCs could care less about their operatives going to jail; they are not happy about losing money. Adversary governments and terrorist groups are more than willing to pay for access to a TOCs well-developed network of money launderers, cyber criminals, black bag experts, etc. At this juncture, no one really knows how much money TOCs are pulling-in to facilitate information warfare projects. It now appears that some of these same shadowy TOCs are acting as conduits for money, planning and organizing insurrection and subversive activities in the U.S.
Ciao,
Steve Miller, IAPWE – Certified & Member
Managing Editor
The Report on National Security Kinetics™
Seattle, WA. USA
vietvetsteve@millermgmtsys.com
RNSK Vol I, Edition 3
Written Statement of
William P. Barr
Attorney General
Committee on the Judiciary
U.S. House of Representatives
July 28, 2020

On July 28, 2020, United States Attorney General, William Barr, will testify in front of the Judiciary Committee of the U.S. House of Representatives. I want to call your attention to Attorney General Barr’s prepared statement released today, July 27th, and will be read into the Judiciary Committee’s proceedings by Barr. The unabridged content of AG Barr’s statement is shown below.
My purpose in bringing this statement to your attention is simply due to the near identical wording in his statement about the current spate of domestic violence issues, and the outcome of that violence, in comparison to my words cited in last weeks RNSK Volume I, Edition 2. It is important to me that my readers recognize that what I write is factual, and correctly analyzed. It is not a fanciful opinion of little value to the discerning public.
Here are some excerpts from Barr’s Statement:
“I want to address a different breakdown in the rule of law that we have witnessed over the past two months. In the wake of George Floyd’s death, violent rioters and anarchists have hijacked legitimate protests to wreak senseless havoc and destruction on innocent victims. The current situation in Portland is a telling example. Every night for the past two months, a mob of hundreds of rioters has laid siege to the federal courthouse and other nearby federal property.
What unfolds nightly around the courthouse cannot reasonably be called a protest; it is, by any objective measure, an assault on the Government of the United States.
Largely absent from these scenes of destruction are even superficial attempts by the rioters to connect their actions to George Floyd’s death or any legitimate call for reform.
Nor could such brazen acts of lawlessness plausibly be justified by a concern that police officers in Minnesota or elsewhere defied the law.
Remarkably, the response from many in the media and local elected offices to this organized assault has been to blame the federal government. To state what should be obvious, peaceful protesters do not throw explosives into federal courthouses, tear down plywood with crowbars, or launch fecal matter at federal officers. Such acts are in fact federal crimes under statutes enacted by this Congress.”
I invite you to read the rest of AG Barr’s prepared statement, and watch his Congressional testimony on July 28th at 10am EDT. Most major television news outlets will carry the proceedings live.
Ciao,
Steve Miller
Editor
The Report on National Security Kinetics™
Seattle, WA. USA
vietvetsteve@millermgmtsys.com